What is Phishing?

Phishing is when cybercriminals send malicious emails to scam internet users. It is a form of social engineering in which scammers use human psychology and manipulate people to act without thinking. The aim is to access sensitive user data such as financial information, system credentials, credit card number, etc.
The phishing emails sent appear to come from a reputable source, and victims are tricked into opening them. Once opened, these emails spread malware and steal data. Usually, techniques such as forgery, imitation, and misdirection play an integral role in phishing attacks.
History of Phishing
You might think of phishing as a new concept, but it has been in use since the mid-1990s. It all started with hackers masquerading as AOL employees to “fish for” information. As AOL was a renowned content system at that time, these scammers were successful in duping victims. They made them divulge their credentials and then hijacked their accounts.
Then in the 2000s, cyber phishing became more prominent in the banking sector. Cybercriminals found bank accounts more profitable, so they lured users into revealing their financial credentials. Phishing emails imitating bank notices were sent in bulk to steal funds of unsuspecting users.
With time phishing has evolved, and more variations are coming out, such as Paypal Phishing, Amazon phishing, Apple Phishing, Spear Phishing, etc. Scammers are getting more advanced, and they imitate reputable organizations by using sophisticated emails that resemble genuine ones. To date, phishing continues to be a problem that online communities face every day.
Phishing a Problem that Prevails
Phishing is widely used to defraud people as it is cheap to conduct. Email addresses are easy to obtain, and the cost of sending emails is zero. Therefore phishing emails are an easy source of money for cyber-criminal.
However, the effects of phishing are not cheap. The cost to society, on the whole, is enormous as millions of people get scammed daily. The individual amounts may be small, but these add up to billions when aggregated. According to the FBI’s IC3, a loss of over 1.8 billion was reported due to phishing.
Apart from financial loss, phishing has also caused significant data breaches. In the corporate world, phishing is often used to gain a foothold for a larger attack. Like the 2013 Target breach, many data breaches start with a single phishing email and then snowball into massive scandals.
Phishing attacks also have negative social consequences. As phishing emails can reveal Personally Identifiable Information (PII) like tax records, medical info, and financial data, it raises privacy concerns. Moreover, phishing can also give cybercriminals direct access to social media, and other accounts, causing these platforms to crash.
Phishing Statistics
As phishing attacks have devastating results for both individuals and organizations, they shouldn’t be ignored. By looking at the phishing statistics mentioned below, you can understand its prevalence and seriousness:
- 2020 alone reported 241,324 phishing attacks
- There was a whopping increase of 110% in phishing incidents between 2019 and 2020.
- Out of every 100 U.S. survey respondents, 75 have fallen prey to phishing attempts.
So everyone should learn about phishing to protect themselves. Read on to find more details on this massive problem that prevails.
Identifying a Phishing Email
The first thing people should know to protect themselves from phishing attacks is how to identify a malicious email. These emails contain a typical pattern that can be easily identified:
The Wording:
Most scammers use fear to bait innocent users. They create a sense of urgency in their email so that readers act without thinking. Unfortunately, even people with phishing knowledge can fall prey to these scams as fear gets them better.
Most phishing emails tell users that their accounts will be restricted or malware will spread on their devices if they don’t click on the given link. The link is what spreads malware and gives hackers access to sensitive data.
Sometimes cyber criminals use incentives to lure curious minds. It is common for attackers to use wording like Invest $40 to get a return of $400, you just won a lottery ticket of $1000, etc. They make it sound genuine and lucrative so that users ignore the warning signs and fall for them. As most users think there is little to lose, they respond to such emails and end up losing a lot.
The following illustrates a standard phishing email:
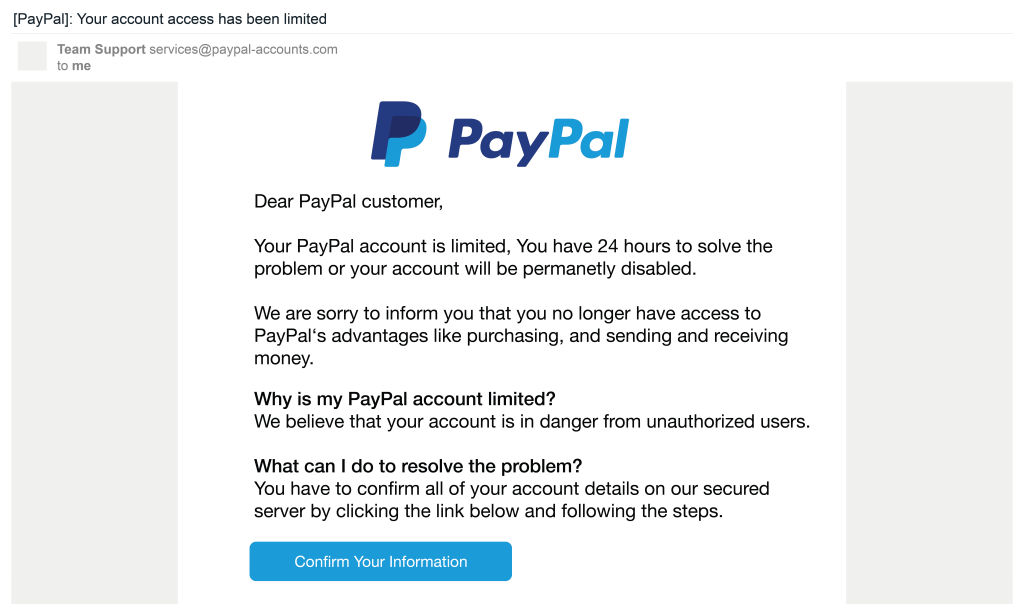
As you can see above, the greeting of phishing emails is generic as sent in bulk. So be very cautious and keep your eyes open. If you are not sure whether a mail is genuine or not, check its sender’s address to determine its legitimacy. If it is a phishing email, there will be a slight discrepancy that can give you a red alert.
The Mechanism Used
After making the email body look genuine, what comes next in phishing emails is usually a mechanism to steal information. Mainly scammers rely on three ways. Either they attach a malicious file, insert a web link, or use fraudulent data-entry forms. We have mentioned each of them separately.
Malicious Web links
This is the most common mechanism used by scammers. In this technique, scammers insert malicious links that transport users to phishing websites or impostor pages infected with malware.
These URLs are disguised to look like genuine links from a reputable site but have minor syntax differences. They can also be embedded in logos and images present in the email. So don’t accidentally click on anything.
Phishing links are more viable than attachments and data forms as users find them less risky. They click on them without much thinking and get trapped easily.
Here is an example of an email containing a malicious link.
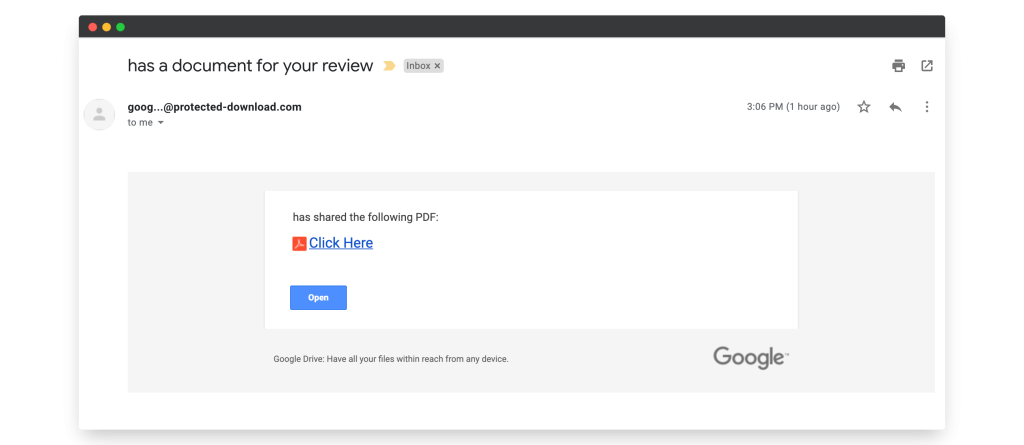
Malicious Attachments
Instead of a web link, phishing emails can have files attached to them. They imitate legitimate attachments but are infected with malware that compromises your computer’s operating system.
The files usually contain a Ms. Office document with a malicious macro or a shell script. These, when downloaded, spread malware such as ransomware which freezes the files on a PC. These files can also be used to install a keystroke logger on your device to track everything you type, like passwords and other confidential info.
Ps: It is essential to realize that phishing containing such malware doesn’t pertain to one device. They spread the infections from one system to another via connected networks, cloud systems, and shared hard drives. Therefore phishing can spread at a swift pace.
Here is an example of an email containing a malicious attachment
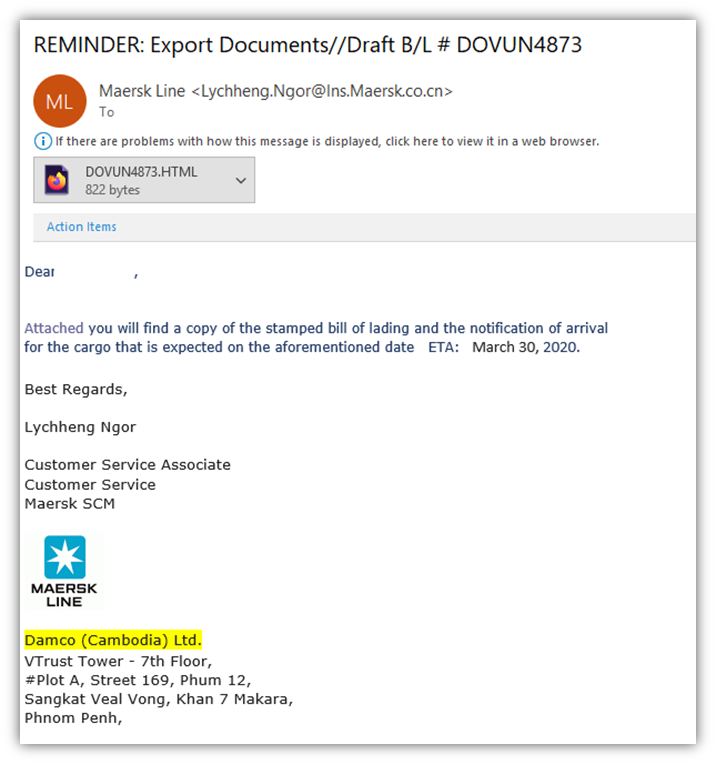
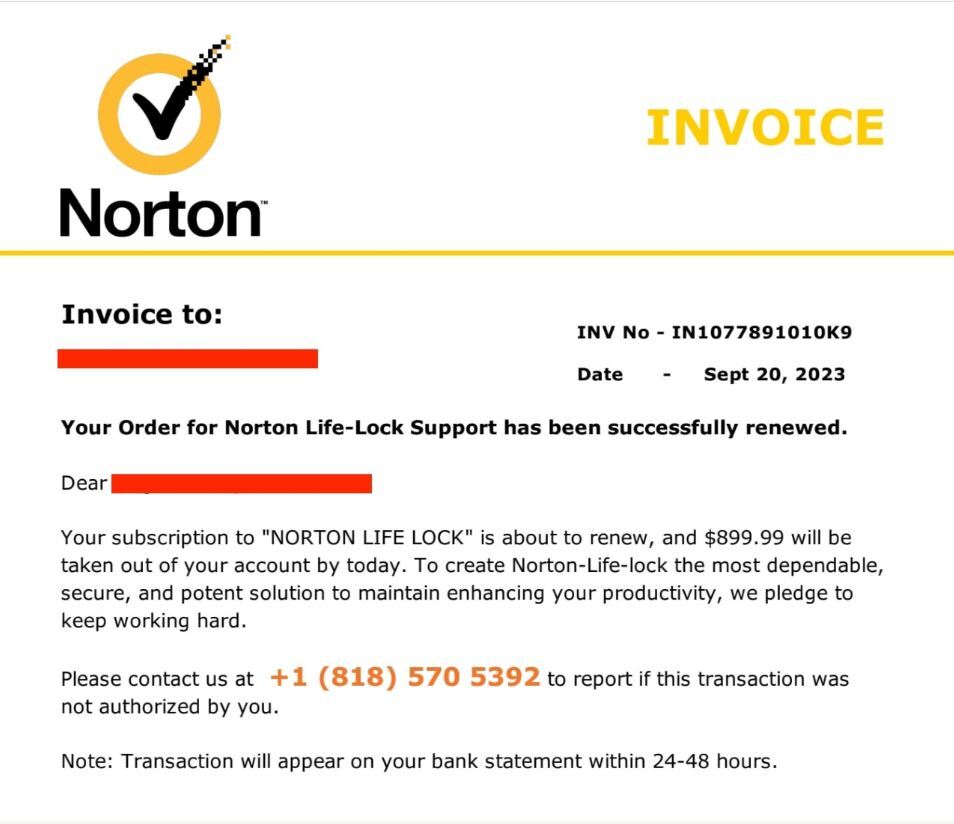
Fraudulent Data Entry Forms
Another common mechanism used in phishing emails is Data Entry Forms. They are mainly designed to accumulate sensitive information like user IDs, credit card numbers, and passwords. The emails are written in a tone that prompts the reader to fill in and submit information on the spot.
Once the users hand in their info willingly, cybercriminals can misuse it for personal gains. Usually, scammers imitate government agencies and persuade unsuspecting individuals to fill out fraudulent forms for tax returns and other civil purposes.
But, you should know better than governments don’t contact citizens over emails nor ask for confidential data via such channels. So these forms should raise a red flag.
Here is an example of a fake email that contains a data entry form:
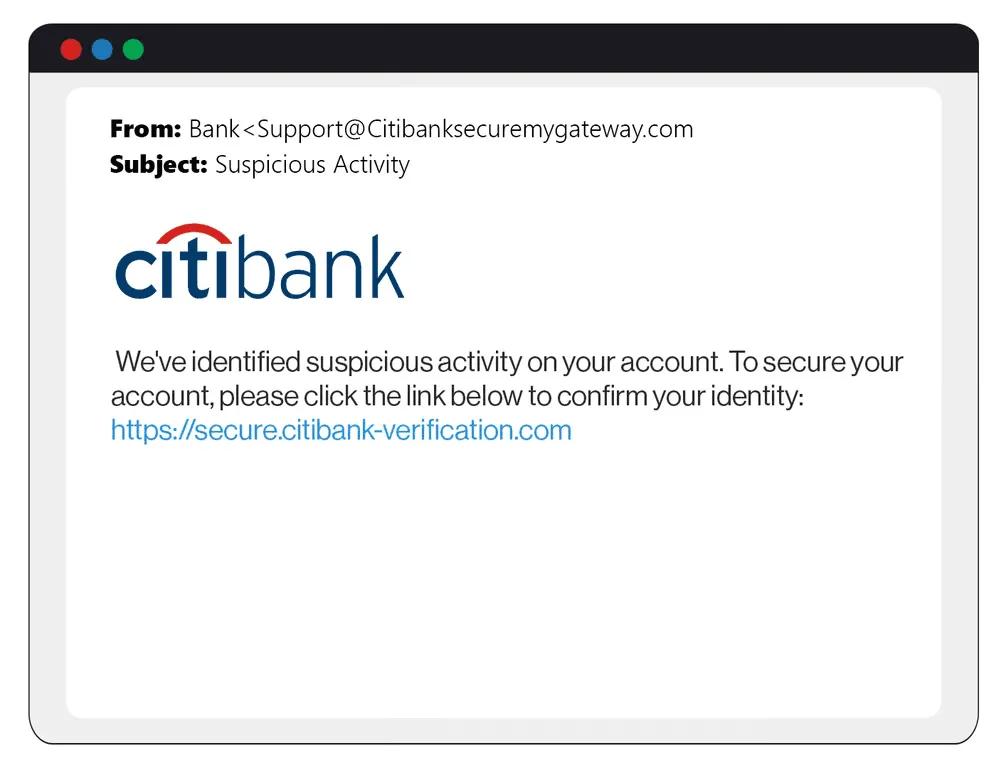
Subject Line
The subject line is another vital aspect of the email that can help you distinguish between legit and phishing emails. In a phishing attack, the subject line plays a crucial role as it determines whether the user will take the bait or not.
So attackers ensure that the subject of the mail either instills fear or curiosity. Both of these emotions, if used well, can make users click on malicious emails.
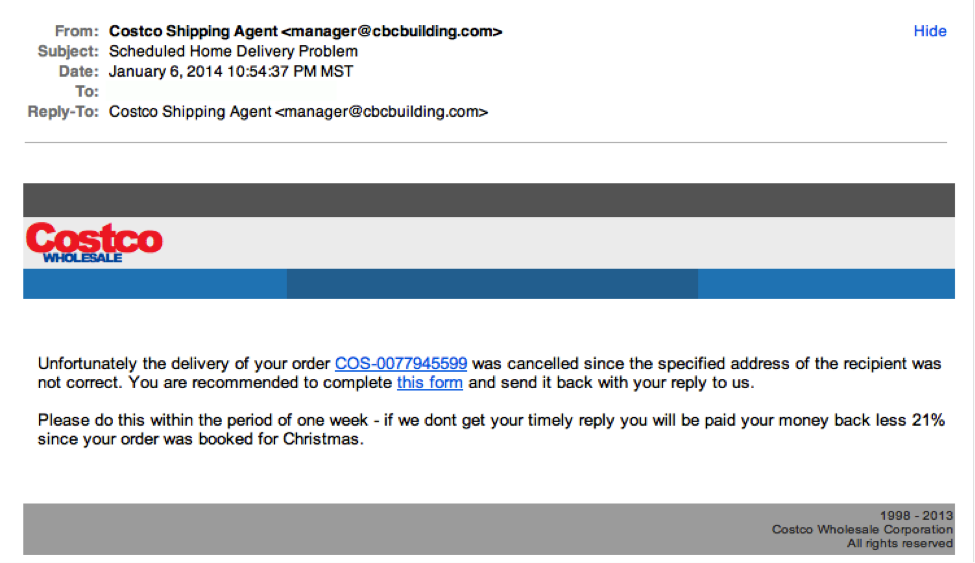
Usually, subject lines highlight user pain points such as shipping problems, bank account issues, etc. If a user is not vigilant about the domain in the sender’s address, he or she can easily be tricked into opening the email. Once an email is opened, scammers’ chances of divulging sensitive information increase.
Here is an example of an email with a generic subject line that most people fall prey to:
Types of Phishing Attacks
Even after knowing the basics of phishing, users, including security experts, can fall prey to such attacks. This is because cybercriminals keep updating their methods. With the advancement in technology and increase in online transactions, Phishing attacks are also evolving, making them harder to evade.
Phishing is no longer limited to bulk spam and simple data theft. Instead, attackers are coming up with new ways to lay out massive campaigns. These attacks can be directed at anyone, depending on the type of phishing.
The significant types of phishing include:
1. Spear phishing:
A targeted form of phishing is in which personalized emails are sent to specific individuals, especially highly-ranked employees and sensitive information holders.
2. CEO fraud:
This is a form of spear phishing, but instead of targeting employees high up in the organization, it attacks junior employees. Scammers imitate senior officials like CEOs to pressure their subordinates into transferring money or acting unethically.
3. Smishing:
This is short for SMS phishing, in which scammers use SMS messages to trick users into opening malicious websites.
4. Vishing:
Voice phishing is a form of phishing that utilizes voice-changing software and targets victims by leaving a very persuading and urgent telephonic message.
5. Amazon phishing and Paypal Fraud Emails
Amazon, eBay, Apple, and Paypal are big players in their respective industries; thus, they are big targets for scammers. With millions of users on these platforms, cyber-criminals find sending emails imitating these reputable brands convenient. These include but are not limited to; fake PayPal emails, apple phishing emails, amazon scam emails, apple phishing emails, etc.
6. “Evil Twin” Wi-Fi:
As the name suggests, in this phishing attack, scammers use free Wi-Fi and trick users into joining a malicious hotspot. Once connected with their victim, they misuse it to conduct man-in-the-middle exploits.
However, remember phishing is not just limited to the types mentioned above. With time more forms are coming to light. In addition, as new online platforms are becoming popular, they are giving birth to different phishing types. For example, a rise in Netflix users has made Netflix scam emails more common.
So, to protect yourself and your organization, you should be aware of the various forms phishing can take and then apply measures accordingly. To make it easier for you to comprehend how phishing occurs, we have included some familiar places where phishing can be found.
Phishing Around You
Phishing is everywhere around you. It is essential to realize that any commoner can fall prey to these attacks if they access the internet and its tools. You can even face the consequences of a phishing attack even when you are not directly involved.
So being cautious is the only way to protect yourself from phishing and its many forms; we have listed a few places where phishing emails are commonly found:
In Personal Life
- Bank accounts.
- Credit Transactions
- Tax returns
- Online Purchasing
- Loans and mortgages
- Social media.
At Work
- Transfer of Corporate funds.
- Loss of Confidential Information regarding customers and employees.
- Exposed Trade Secrets
- Frozen systems and Infected files
- Damaged Reputation.
- Penalties due to compliance violations.
- Loss in Market Share
- Declining investor confidence.
In Industries:
- E-commerce
- Financial Markets
- Payment systems
- IT and Telecommunication companies.
- Delivery companies.
Popular Imitated Brands:
- Amazon
- Bank of America
- Microsoft
- Apple
- FedEx
This is by no means a complete list, as phishing attacks can be conducted anywhere. It is just there to give you an example of how widespread phishing is and why awareness and protection are much needed?
Phishing Protection
As phishing has become sophisticated, with scammers using phishing kits to go undetected, the need for protection has become even more evident. Additionally, phishing campaigns have gone massive, with Criminals using dozens of domains to target additional people.
As the cybersecurity landscape is continuously evolving, it has become critical for corporations to educate their employees on the latest phishing techniques and how they can be prevented. Keeping them aware of the latest threats and instilling cyber security can help mitigate successful phishing attempts.
Here are some ways to enable phishing protection in organizations:
1. Anti-phishing Training Suites
Employees can be made aware of phishing scenarios through training suites that contain simulation exercises and real-world examples. Usually, security experts send lookalike phishing emails to employees and check whether they can identify it or not.
This practical application helps employees recognize phishing beforehand and reduce the risk of being compromised during actual attacks in the future. Training employees in such ways ensures that the organization does not end up as the next phishing victim and protects employees in their personal capacity.
2. Email Gateway Solutions
Organizations can install solutions that can catch and classify phishing emails. One of the most effective tools to identify and filter suspicious emails is Email Gateway Solutions.
By using analytics, this monitoring tool constantly watches the traffic for unusual patterns and quarantines any suspicious messages. They alert the administrator if there are many in-page exploits and downloads. This information can then be used to warn employees, thereby reducing the chances of a successful phishing attempt.
3. Anti-Virus Installation
Even though this doesn’t come under Phishing protection, it helps you mitigate damages from a Phishing attack. If you fall prey to a scam, installing antivirus software on your device can help detect and remove the malware that ensues. Just ensure that your antivirus software has the latest patches installed and is up to date.
4. Report Phishing
This is something to be conducted after a phishing attack. If you have fallen prey to a phishing attempt or believe yourself to be the next target of a phishing scam, you must report it to the proper authority.
On a corporate level, you can report it to the IT department, which can review it and take preventive measures. For individuals, it is best to report phishing to the FTC (Federal Trade Commission), which can catch scammers and even help you mitigate your loss!
Conclusion
Skysnag’s automated DMARC solution strengthens protection against phishing and spoofing by confirming that an email message came from the domain it claims to have come from. Skysnag generates DMARC reports for you that aid in investigating potential security problems and identifying potential risks from phishing attacks. Get started with Skysnag and sign up using this link.






