The Skysnag Blog
What is DMARC?
DMARC stands for “Domain-based Message Authentication, Reporting & Conformance”. It is an open email authentication, policy, and reporting protocol that enables domain owners to combat phishing attacks.
Why should we implement DMARC?
DMARC’s purpose is to protect domains from unauthorized use, commonly known as email spoofing, and help reduce the risk of Business Email Compromise (BEC) attacks, phishing emails, malware, and other cyber threat activities.
Use our free DMARC Checker to run a quick analysis that will inform you of the status of your domain, as it examines DMARC, SPF, and DKIM. You will then notified of the next steps you must follow to achieve compliance.
How serious is this?
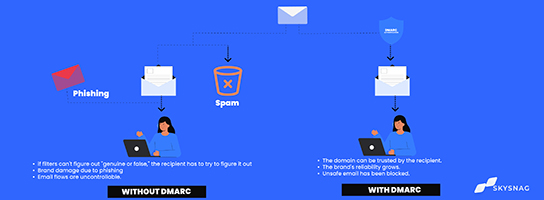
Email impersonation bypasses any security measure in place, employee training, SOC, 2FA, HTTPS, strong passwords, and anything else that is already in place.
Attackers could easily inspect whether an organization domain name can be impersonated by querying the DNS for the public records. If no DMARC enforcement is in place, a domain name can be spoofed.
Attackers latch onto a company’s good domain reputation to deliver spam mail and sometimes direct impersonation attacks – they continue doing this until the domain ends up on a blacklist.
Result?
Spam and Junk.
Spam and Junk have become a mystery for many companies, to an extent that they take the action by informing their clients to check their Junk/Spam folders. If an email is valid, it should always land into the Inbox folder and never elsewhere.
Why doesn’t everyone have DMARC already?
When Email was initially built a long time ago, no one expected that in the future, third-party mail senders will send an email on your behalf. SMTP never had authentication, which made email impersonation and spoofing possible – allowing attackers to send email from any domain name.
Security standards named SPF, DKIM, and DMARC were introduced to correct this loophole. But the fix had to be made on the DNS, only by domain owners, and required numerous monitoring actions – this made it challenging and time consuming – leaving 90% of businesses today unconfigured.
Why does this happen?
- Excessive usage of your domain name in an unauthorized way, meaning spoofers send out emails from your domain in mass.
- Your emails are being sent from mail senders while being misconfigured.
Skysnag helps you discover the next level of autonomous email authentication while taking care of your domain reputation, DMARC enforcement settings, and SPF/DKIM alignment, all in an automated fashion.
Regain your email reputation and ensure every email that is sent from your domain name is going out authenticated.
- Say no to Junk.
- Say no to Spam.
DMARC Policies
The DMARC protocol comes with multiple options and levels of policy enforcement:
1. Monitor policy: p=none
The p=none is a monitoring policy which does not take any action when DMARC fails, yet it allows a domain owner to gain insight into what is happening on their domain. It is the policy that all domain owners start with and it leads the way to the ideal DMARC enforcement status.
2. Quarantine policy: p=quarantine
This is a stricter policy than the monitor policy whereby a domain owner can set a percentage of how many emails failing DMARC checks can get into the inbox and how other emails can land in the spam folder. You have probably seen some domains with a 30% p=quarantine, which means 30% of emails failing DMARC will land in the recipients’ inboxes. Domain owners usually start with a low percentage, but as they gain more confidence that they won’t lose a good email, the percentage increases.
3. Reject policy: p=reject
This policy is the ultimate policy every domain should reach. It is the policy that rejects every email that fails DMARC checks, and guarantees all other email is properly authenticating DMARC and to be delivered to the receiver’s Inbox folder.
Why Does DMARC Fail?
DMARC can fail due to two main reasons:
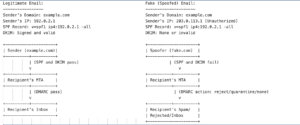
Either the DMARC record is misconfigured or the domain name is being used by attackers. Let’s delve deeper into this.
1: DMARC Alignment Failures
DMARC uses [identifier alignment] to ensure that the message is coming from the domain that you specified in the “From” section of the email header. This process can be possible if your DKIM and SPF records are properly configured.
Create a Skysnag account to generate your DMARC record.
If your records are misconfigured, DMARC will fail even for authentic emails, so make sure your SPF record has your sending domain IP and if there is any third party sending on your behalf, they are included in your SPF. As for DKIM, make sure that your domain key matches the From header key.
For DMARC to pass, either SPF or DKIM has to be aligned and you can set alignment modes to strict and relaxed. When setting alignment modes to the strict modern and you are sending emails from a subdomain, make sure to allow explicit permission for authentication from your subdomain.
2: Email Forwarding
Emails pass through an intermediary server when forwarded. During this process, the SPF must fail since the IP address of the forwarding server does not match the original domain’s SPF.
DKIM’s role here is to have the digital signature of the email match the public key signature that the receiving server checks.
Yes, DKIM does not care about IPS as it will check the receiver DNS which is a constant and thus does not fail. Making sure SPF & DKIM records are properly configured and analyzing DMARC reports is crucial to avoid deliverability issues with forwarded emails.
3: Missing Sending Sources In DNS
When you enforce DMARC, it is a necessity to add the records of any third party sending service sending email on your behalf to your DNS, since authentication will fail due to failure in SPF alignment as MTA will not find the sending IPs in your records, resulting in authentication failure of legitimate messages. To solve this, Skysnag automates the addition of your valid IP addresses to prevent SPF alignment failure.
Conclusion
Skysnag’s automated software safeguards your domain’s reputation and keeps your business away from compromised business emails, password theft, and potentially significant financial losses. Unlock insights, bypass email authentication configuration issues including SPF and DKIM; and protect your domain from spoofing with strict DMARC enforcement, all autonomously with Skysnag. Get started with Skysnag and sign up using this link for a free trial today.
Check your domain’s DMARC security compliance
Enforce DMARC, SPF and DKIM in days - not months
Skysnag helps busy engineers enforce DMARC, responds to any misconfigurations for SPF or DKIM which increases email deliverability, and eliminates email spoofing and identity impersonation.