What is a DMARC Policy?
DMARC POLICY?
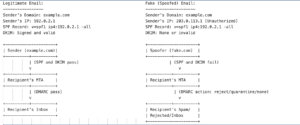
A DMARC policy is an email authentication policy that allows domain owners to specify how their emails should be handled if they fail DMARC authentication. DMARC policies can be used to tell mail clients to reject or quarantine emails that fail DMARC authentication or to allow them to be delivered to the recipient’s inbox.
DMARC Policies
DMARC policies include:
- Reject: All emails that fail DMARC authentication will be rejected and not delivered to the recipient’s inbox.
- Quarantine: All emails that fail DMARC authentication will be delivered to the recipient’s spam folder instead of their inbox.
- None: No action will be taken from receiving servers, and emails that fail DMARC authentication will be delivered to the recipient’s inbox.
Enforce DMARC policy in steps?
A DMARC policy can be set to ‘none’, ‘quarantine’, or ‘reject’.
The percentage tag pct instructs ISPs to only apply the DMARC policy to a certain percentage of emails that fail the DMARC check. This allows organizations to evaluate the impact of the enforced policy before fully implementing it.
Enforcing the policy in small steps allows organizations to evaluate the impact of the enforced policy. This way, it can be determined if the enforcement results in a loss of legitimate email. Since enforcement will only impact a small percentage of all emails, it will not result in a massive loss of legitimate emails if the setup is done incorrectly.
Utilize the PCT tag for smooth DMARC Enforcement
Using the percentage tag, you can enforce your DMARC policy in small steps. This tag tells ISPs to only apply the DMARC policy to a certain percentage of the emails that fail the DMARC check. For example, setting the percentage to 50 will tell receivers to only apply the policy 50% of the time against emails that fail the DMARC check. Note that this will only work for the quarantine and reject policies and not for the none policy.
A DMARC deployment always starts by publishing a DMARC policy of none, which only monitors email sources. After reports come in, organizations can start improving the alignment of all legitimate email sources. Once all sources are aligned, the DMARC policy can be slowly moved towards enforcing quarantine in steps of 5%, 10%, 25%, and 50% to 100%. Once the 100% reject policy is published, DMARC is fully deployed, and all emails that fail the DMARC check will be rejected.
How do I check my DMARC policy and how Skysnag automated the process?
Placing a static p=none DMARC record takes 5 minutes and is fairly simple, but what is is difficult is getting to a strict enforcement policy safely without losing good email.
Skysnag was built to safely enforce your domain with DMARC. To start your DMARC journey, scan your DMARC compliance here and follow the onboarding steps right from the scanner.
Skysnag is an enforcement-focused solution that prioritizes companies getting to enforcement policies (p=reject) securely and with little effort, saving hours and avoiding any risks during the process.
Do I need a DMARC policy?
DMARC enforcement ensures that only valid email senders can send emails from your domain. This way, you can be sure that your visitors or customers will only see emails you have authorized. Every domain owner should have DMARC to protect their domain and email identity.
How do I set up a DMARC Policy
To set up a DMARC policy, you will need to create a DNS TXT record with the following format; if you decide to use Skysnag for your DMARC project, the record will be uniquely generated for your domain and will dynamically modify itself to reach higher levels of enforcement, without recurrently modifying your DNS.
An example of a DMARC record is as such:
_dmarc.yourdomain.com IN TXT “v=DMARC1; p=reject; rua=mailto:[email protected]
Replace yourdomain.com with your domain name and [email protected] with the email address you want to receive DMARC reports.
The p=reject value tells mail servers to reject emails that fail DMARC authentication. You can also use the p=quarantine value, which tells mail servers to mark emails as spam if they fail DMARC authentication.
Troubleshooting with DMARC Policies: Typical Issues
You must set up DMARC records to work with SPF and DKIM to avoid getting false-negative rates. By utilizing both of these protocols, DMARC can fix the majority of difficulties.
If you’ve set up DMARC to use both SPF and DKIM and you’re still getting a lot of false negatives, check the DMARC record and make sure it’s set up correctly. If this is the case, look into the level of enforcement that has been established. Spoofed emails will be transmitted without an inspection if a DMARC policy is submitted to p=none.
As a result, it’s also a good idea to avoid utilizing an “sp” tag in your DMARC record, as it applies the same policy from a top-level domain to all subdomains below it. If the top-level domain is set to p=none, p=quarantine, or p=reject, any domains beneath it will be the same, increasing the chances of false positives and negatives, depending on the setting. It’s best to set up DMARC for each domain independently.
Understanding DMARC Aggregate Reports
DMARC reports will be sent to you regardless of the policy you select.
- If you select the “none” policy, a report of DMARC authentication results will be sent to the email address specified in the policy. You’ll also notice the email’s sender and maybe the IP address.
- Your DMARC report will include the same data with the “quarantine” policy, but emails that fail DMARC authentication will be quarantined in the spam or a similar folder.
- Finally, if you use a “reject” policy, your DMARC report will include information about emails that were blocked from reaching an inbox. For emails that fail DMARC authentication, certain mailbox providers will include detailed “failure samples,” often known as forensic reports.
DMARC reports are sent to the email address specified in the DMARC record and are in XML format. These reports will assist you in determining which fraudulent emails were not stopped valid emails were.
Full DMARC enforcement
Creating a DMARC record is easy, but reaching to enforcement levels safely is difficult. Skysnag streamlines and simplifies the entire DMARC setup, administration, reporting procedures, and enforcement, reducing the time to complete DMARC policy enforcement substantially.
Create a Skysnag account to generate your DMARC record.
Our automated DMARC solution strengthens protection against phishing and spoofing by confirming that an email message came from the domain it claims to have come from.Get started with Skysnag and sign up using this link to completely secure your email and ensure your organization remains free of cybercriminal activity.