Email has been a cornerstone of business communication for decades, yet for a long time, it lacked the essential authentication needed to prevent cyber threats. This vulnerability allowed attackers to spoof senders and impersonate brands, fueling widespread phishing and email fraud that cost businesses billions.
To combat this, DMARC (Domain-based Message Authentication, Reporting, and Conformance) was introduced as a protocol to verify sender identities and protect domains from abuse. Since its inception, DMARC has evolved significantly, and as of 2024 and 2025, major email providers are enforcing it, making email authentication a critical component of business security.
In this blog, we’ll explore the origins of DMARC, how it developed over time, and why implementing it is now a must for all businesses.
What Is DMARC (And Why It Exists)
DMARC is an email authentication protocol that works with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to verify that the sender is authorized to use a domain.
It was developed in response to the rise in phishing attacks and domain spoofing. Without DMARC, anyone can send an email “from” your domain, eroding customer trust and putting your brand at risk.
The Evolution of DMARC: A Timeline
2010–2011: DMARC Is Born
Although SPF and DKIM improved email security, they only partially addressed spoofing and phishing. This led to the creation of DMARC – Domain-based Message Authentication, Reporting, and Conformance. In 2010, major industry players including PayPal, Microsoft, Google, and Yahoo! collaborated to develop DMARC, aiming to give domain owners more control and receive feedback about email authentication.
The first DMARC specification was released on January 30, 2012, marking a new milestone in email security.
2012–2020: The Slow Adoption Phase
Despite its potential, DMARC adoption was slow due to technical complexity and lack of awareness. Many organizations lacked the expertise to implement SPF and DKIM, prerequisites for DMARC deployment. Large financial institutions and tech companies begin implementing DMARC. Still, adoption is voluntary. Many businesses view it as “nice to have,” but not essential.
In 2015 and 2016, industry giants such as Google and Yahoo! started enforcing stricter DMARC policies, signaling that domains ignoring DMARC risked deliverability issues.
2021–2023: Spoofing Surges
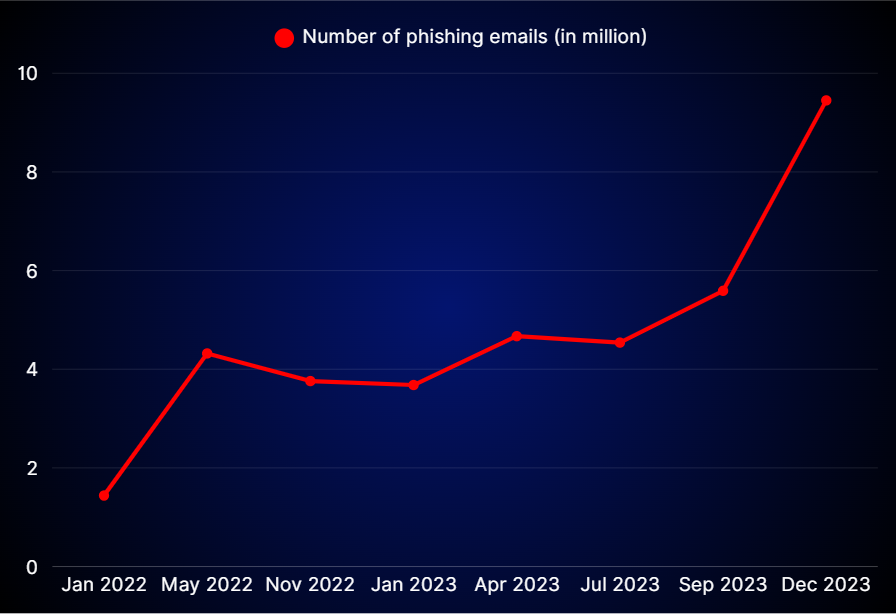
In December 2023, spoofing and phishing reach record highs as 9.45 million phishing emails are detected globally, up from 5.59 million in September (Statista). As industry pressure grows, DMARC visibility is increasingly integrated into cybersecurity tools, though enforcement remains rare. Skysnag’s all-in-one platform automates DMARC enforcement, helping organizations protect themselves against spoofing attacks by achieving complete email compliance in days, not months.
Start Free TrialFebruary 2024: Google & Yahoo Enforce DMARC for Bulk Senders
Google and Yahoo announce that bulk senders (sending 5,000+ emails/day) must have a valid DMARC policy in place, or risk emails being rejected or sent to spam.
Requirements include:
- A domain with a valid SPF and DKIM record
- A DMARC policy (at minimum
p=none) - TLS encryption
- One-click unsubscribe
Failure to comply with Google and Yahoo email sender requirements results in reputation damage and delivery failures.
May 2025: Microsoft Joins the Push for DMARC Compliance
Microsoft begins actively enforcing DMARC across Outlook and Exchange Online for business senders on May 5, 2025. Authenticated email becomes the standard, even for low-volume senders.
From this date forward, Microsoft rejects emails that don’t meet strict authentication requirements. If a domain fails DMARC alignment with SPF or DKIM, the following error may appear:
550 5.7.515 Access denied, sending domain [YourDomain] does not meet the required authentication level.
Why This Matters Now
If you’re sending email – whether through HubSpot, Mailchimp, Google Workspace, or your own servers – you must explicitly authorize those platforms in your domain’s DNS records.
Without that authorization:
- Your emails may be marked as spam or rejected outright
- You lose visibility into who’s spoofing your domain
- Your domain can land on blacklists
- You lose control over your brand’s email reputation
The Role of SPF, DKIM, MTA-STS, TLS-RPT & BIMI
While DMARC gets most of the attention, it’s part of a full suite of authentication protocols that together:
- Authenticate your identity (SPF, DKIM)
- Secure the connection (MTA-STS, TLS-RPT)
- Visually reinforce trust (BIMI, with your logo and verified blue checkmark)
These protocols work together to secure your domain, improve email deliverability, and ensure your emails land where they belong: the inbox.
Final Thoughts: Email Authentication Is Not Optional
The message from Google, Yahoo, and Microsoft is clear: Authenticate or risk getting blocked.
DMARC and related protocols are no longer best practices, they’re baseline requirements. If you haven’t already, now is the time to get your domain configured correctly, enforce your DMARC policy, and protect your reputation.
Skysnag automates the entire email authentication process – from SPF, DKIM, and DMARC setup to MTA-STS, TLS-RPT, BIMI, and blacklist monitoring – all in just a few clicks, with no technical expertise required.
Sign up now and try it free or get a domain health report in under 30 seconds.
Ready to secure your sending identity and protect your domain reputation? Sign up today.
Get started