What is the NIST Cybersecurity Framework? The Ultimate Guide to DMARC

History of NIST
The National Institute of Standards and Technology (NIST), a part of the U.S. Department of Commerce, develops standards and best practices to help organizations improve their cybersecurity posture. In 2013, Executive Order 13636 directed NIST to create a Cybersecurity Framework (CSF) that would:
- Identify and manage cybersecurity risks across industries
- Be flexible, repeatable, and cost-effective
- Encourage innovation and resilience
- Enable cross-sector collaboration and performance measurement
The result: a framework used globally by private and public sectors to manage cybersecurity risk regardless of size, industry, or geography.
Why the Framework Matters
Cybersecurity threats are accelerating, and organizations need a unified approach to manage risk, protect systems, and respond to incidents. The NIST Cybersecurity Framework (CSF) provides a common language and structure to achieve that.
The framework originally centered around five core functions: Identify, Protect, Detect, Respond, and Recover. With the release of version 2.0, a sixth function, Govern, was added to emphasize the role of organizational leadership, policy, and risk management in cybersecurity.
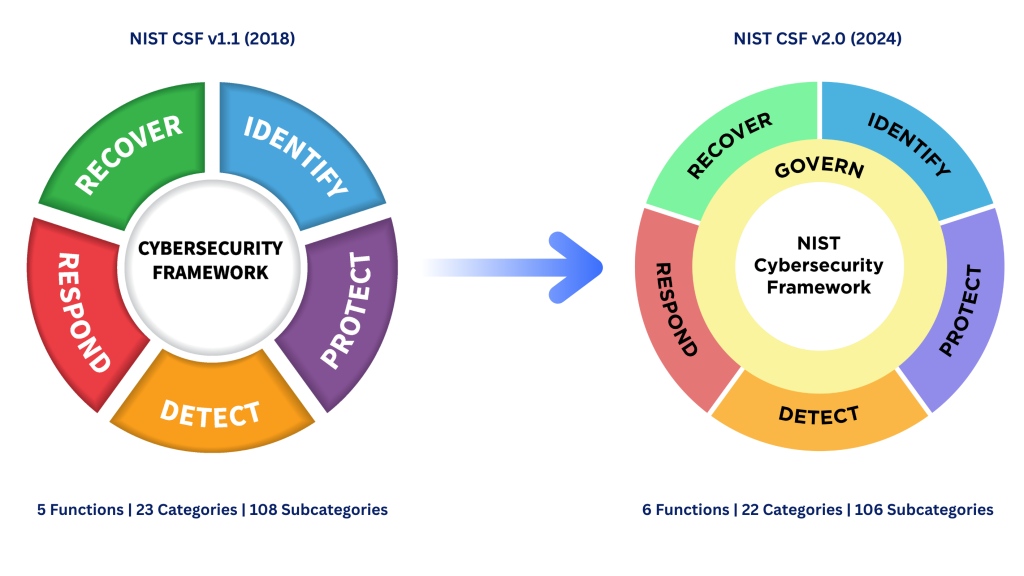
Together, these functions enable organizations to prepare for, withstand, and bounce back from cyber events – and they’re directly relevant to securing the most commonly targeted vector: email.
How DMARC Fits into the NIST Cybersecurity Framework
DMARC (Domain-based Message Authentication, Reporting & Conformance) is an email authentication protocol that stops domain spoofing and impersonation. Though it’s a DNS-based standard, it maps cleanly into the NIST CSF because of how it:
- Identifies unauthorized use of domains
- Protects recipients from forged messages
- Detects malicious sending sources
- Enables fast response to abuse
- Supports recovery and adjustment post-incident
DMARC isn’t just an email standard – it’s a critical control aligned with modern cybersecurity strategy.
Understanding DMARC
DMARC builds on SPF and DKIM to allow domain owners to:
- Publish policies on how email should be authenticated
- Receive reports on authentication activity
- Enforce rejections of unauthenticated messages
It helps organizations protect their brand, customers, and infrastructure from phishing and spoofing threats.
Since its inception, DMARC has been adopted by organizations globally – from enterprises and universities to government institutions and SaaS vendors.
Core Functions of the NIST Cybersecurity Framework and DMARC
| NIST CSF Function | DMARC Alignment |
|---|---|
| Identify | Analyze your domain ecosystem and email-sending services to understand risk exposure. |
| Protect | Publish DMARC policies to block spoofed email (e.g., p=reject). |
| Detect | Use DMARC aggregate and forensic reports to spot unauthorized use. |
| Respond | Take corrective action against shadow services or misconfigured senders. |
| Recover | Tune authentication policies post-incident to maintain secure communication. |
| Govern | Establish organizational accountability for email security. Use DMARC as a formal policy to prevent domain spoofing, aligned with leadership-driven risk management and compliance goals. |
Implementing DMARC in a NIST-Aligned Way
Just like NIST recommends a seven-step implementation process, DMARC deployment can follow a similar structured approach:
- Prioritize and scope: Identify high-risk domains and email flows.
- Orient: Map current SPF/DKIM/DMARC records and third-party senders.
- Create a current profile: Document authentication status for all domains.
- Conduct a risk assessment: Identify where spoofing could occur or where enforcement would fail.
- Create a target profile: Define enforcement goals (p=reject) and visibility objectives.
- Analyze and prioritize gaps: Address misaligned records, shadow IT, and weak enforcement.
- Implement action plan: Monitor reports, adjust configurations, and move to enforcement.
Benefits of Aligning DMARC with NIST
- Reduces domain spoofing risk
- Improves email deliverability and domain reputation
- Supports incident detection and reporting
- Improves compliance with government and industry frameworks
- Builds trust with customers and partners
Adoption Challenges
Implementing DMARC requires:
- Understanding your full sending infrastructure
- Coordinating with third-party providers
- Analyzing large volumes of XML-based DMARC data
- Continuously adapting to new email sources
Organizations often stall at p=none due to the complexity of moving to enforcement (quarantine or reject).
Leveraging Skysnag for NIST-Aligned Email Security
Skysnag simplifies the journey by:
- Automating SPF, DKIM, and DMARC setup
- Aggregating DMARC reports across providers
- Identifying misalignments in real-time
- Managing enforcement policies across domains
- Ensuring full compliance with the NIST Cybersecurity Framework
Ready to secure your domain?
Start your NIST-aligned email protection journey with Skysnag.
Explore our platform, schedule a demo, or get started for free.
Ready to secure your sending identity and protect your domain reputation? Sign up today.
Get startedSubscribe to our newsletter
Related Resources

NIS2 Across the EU: Germany Leads the Way in Cybersecurity Compliance

How Email Authentication Helps Your Business Stay Compliant with Data Privacy Laws

New Zealand Sets October 2025 Deadline for Strict DMARC Enforcement




