Example of Email-Based Attacks
Over a billion individuals use email on a daily basis across the world. Email has grown to be a significant vulnerability for individuals and companies as one of the most widely used services resulting in a wide spread of email-based attacks. However, there are also others that try to harm our machines that are connected to the Internet, invade our privacy, and disable Internet services. In this article, we shall be looking at the most common email-based attacks.
Examples of Email-based attacks
Some of the most typical email attacks are listed below:
1. Phishing
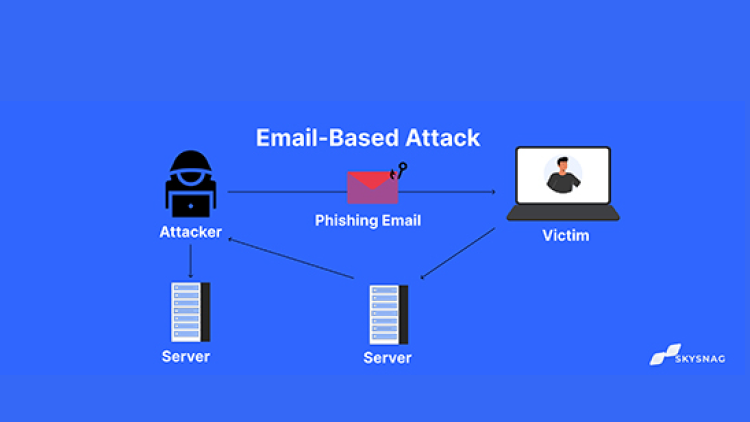
Phishing is a kind of email attack that deceives recipients into divulging private information like passwords, account numbers, or credit card numbers. Attackers frequently send emails that closely resemble official correspondence from a reputable business, such as a bank or online retailer, while assuming the identity of that company. Typically, the email will include a link that takes the recipient to a bogus website that mimics the actual thing. The attacker can access the user’s accounts if they provide their login information or other sensitive data on this bogus website.
2. Spoofing
An email assault known as spoofing involves changing the sender’s address to make it appear as though it is coming from a reliable source. This can be accomplished by altering the “From” field in the email header or by directing email traffic through an attacker-controlled server using a service like Sendmail. The email may attempt to fool the receiver into disclosing private information, including a virus or other dangerous payload, or both.
3. Business email compromise (BEC)
A request for money or sensitive information is typically included in an email that purports to be from a C-level official within a company.
4. Pharming
Even when users write in the right URL, a phishing email assault takes them to a fake website this attack is known as Pharming. Malware that modifies the hosts file on a computer can infect it, or an attacker can modify a domain’s DNS records. Instead of the original website, users who try to visit it are sent to the attacker’s fake one. Sensitive information, such as login credentials, may be stolen using this.
5. Trojan horses
A Trojan horse is a type of email attachment that contains malware. Even though the email and attachment may look legitimate and come from a reputable source, when the victim clicks them, the malware is installed on their computer. Trojan horses can be used to steal data, enslave the machine to a botnet, or even completely wipe the hard disk clean of all files.
6. Viruses
A virus is a harmful email attachment that contains self-replicating code that can infect different systems. Viruses can be used to erase files, take over computers, or steal important data.
7. Worms
A worm is an email attachment that includes malicious software designed to spread to other computers. Worms can be used to delete files, take over computers, or steal important data.
8. Denial-of-service (DoS) attacks
A denial-of-service (DoS) attack is a form of email attack that aims to prevent users from accessing a computer or network resource. The attacker can accomplish this by sending erroneous requests that cause the system to become overloaded or by saturating the target with traffic that it cannot handle. DoS attacks can be used to bring down entire networks, email servers, and websites.
9. Spam
This is a form of email that is frequently sent in mass for commercial reasons. Spam isn’t typically thought of as harmful, although it may be bothersome and challenging to filter. It’s crucial to exercise caution when opening emails from unknown senders since some spam emails may contain malware or links to phony websites.
Conclusion
Skysnag’s automated DMARC solution strengthens protection against email-based attacks by confirming that an email message came from the domain it claims to have come from. Skysnag generates DMARC reports for you that aid in investigating potential security problems and identifying potential risks from impersonation attacks. Get started with Skysnag and sign up using this link for a free trial today.




