Your Domain Is Sending Phishing Emails – Even If You Don’t Know It

Cybercriminals are running spoofing attacks using company domain names. They don’t hack your servers. Instead, they borrow your domain’s reputation to slip phishing emails straight into inboxes.
And if you don’t have DMARC enforced, nothing stops them.
Example: Spoofed Signing Platform Email
Here’s a phishing email we captured – it was sent using a domain name owned by a multinational organization.
The email is indicating DocuSign with the template of DocuSign but it is being sent from a credible organization domain name.
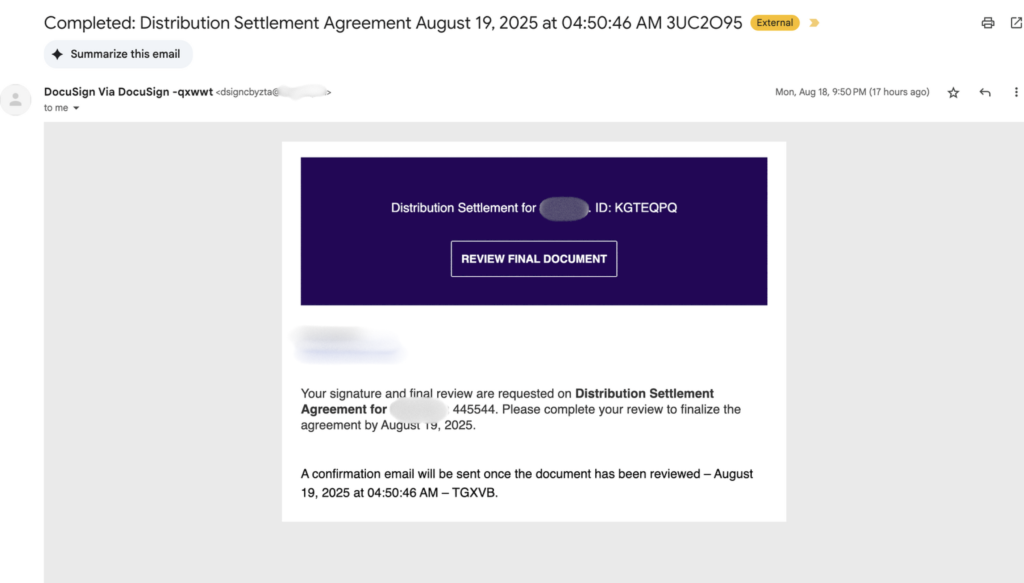
At first glance, the email looks like a legitimate DocuSign request. The sender domain appears to belong to the signing platform, leading the recipient to trust the name and click.
Note: The actual company domain name is withheld here for privacy.
In reality, the attacker is spoofing the company’s domain, taking advantage of the fact that there is no DMARC protection in place.
How did the attacker know?
Because DNS is public. It always has been, and always will be. Attackers can scan DNS records at scale, and when they see a domain with no DMARC record, it’s an open invitation. Even a domain left at “monitoring only” is a high-risk loophole.
This is exactly what attackers look for – the smallest gap. One misconfigured or missing record gives them free rein to send fraudulent emails under your company’s name, delivering theft and fraud while you remain unaware.
Out of Sight ≠ Out of Risk
Without monitoring, this never shows up in your logs. To you, it looks like nothing happened. But in reality, your domain is sending phishing emails to CEOs and individuals you don’t even know.
- We’ve seen spoofed emails pretending to come from large financial institutions.
- We’ve seen contract signature requests using hijacked corporate domains.
- We’ve seen board members and executives directly targeted with spoofed brand names.
The Liability Is Yours
When a victim clicks, they see your company’s name. To them, it’s your fault.
- A spoofed invoice? They’ll assume you lost control.
- A fake contract request? They’ll question your security.
- A phishing link delivered with your domain? They can claim damages.
Your brand and leadership are on the line.
The Fix Is Clear
- Implement DMARC, SPF, and DKIM.
- Monitor your domain for abuse.
- Set DMARC to reject diligently because “none” means open season. Note: manual DMARC enforcement – this can lead to valid emails being blocked.
Leading enterprises protect their domains before attackers exploit them. Skysnag makes it simple to close the gaps, block threats, and achieve full email compliance with Genius DMARC enforcement.
- Request a Free Domain Assessment – get immediate visibility into risks.
- Speak With Our Success Team – tailored guidance for your organization.
- Start a Trial – see how quickly you can enforce protection.
Ready to secure your sending identity and protect your domain reputation? Sign up today.
Get started