How to Configure DKIM for Proofpoint Essentials?

DomainKeys Identified Mail (DKIM) is an email authentication system designed to detect email spoofing. It allows organizations to take responsibility for transmitting a message, while providing a mechanism to verify that the message was not altered during transit. DKIM uses cryptographic signatures and public-key infrastructure to verify that an email message has not been altered during transit, and that it truly came from the claimed sender. Email senders can use DKIM to sign their messages by adding a DKIM-Signature header field to the messages. Email receivers can then use the public key published in the DNS to verify the signature and check that the message has not been tampered with.
Steps to Configure DKIM for Proofpoint Essentials
Each domain that sends email can be individually configured to sign outbound messages with DKIM. To enable the feature, you will need to create a new signing key, add the public key to your DNS zone, and verify that its been added correctly.
1. Navigate to Administration > Account Management > Domains.
2. Select the domain you want to configure and click the vertical ellipsis on the right-hand side of the Domains table.
3. Click the option labeled Configure DKIM.
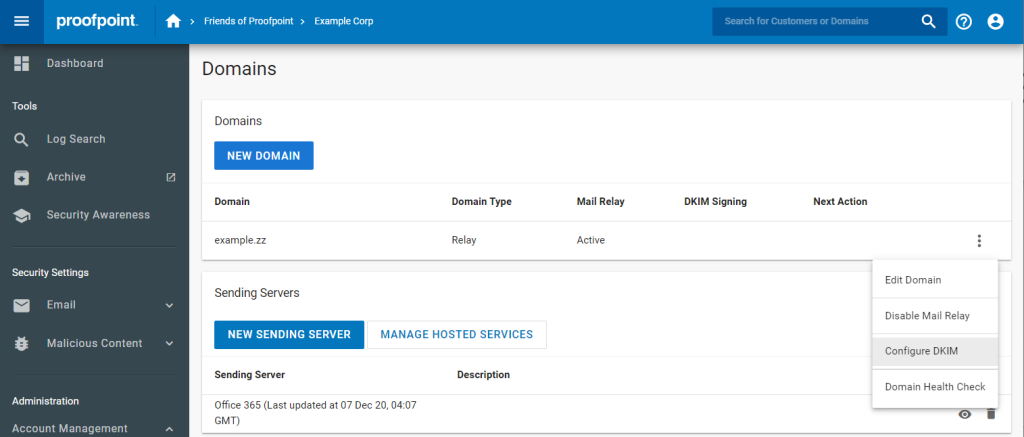
4. A drawer will appear on the right side of the screen, listing all the currently configured DKIM keys. If this is your first time configuring DKIM, no keys will be listed. Click Create New DKIM Signing Key.
5. The form will appear asking you to specify a selector. A selector is used to locate the public key in DNS and is not visible to end users. A value is pre-populated, but you can change it if you’d like. Click Create.
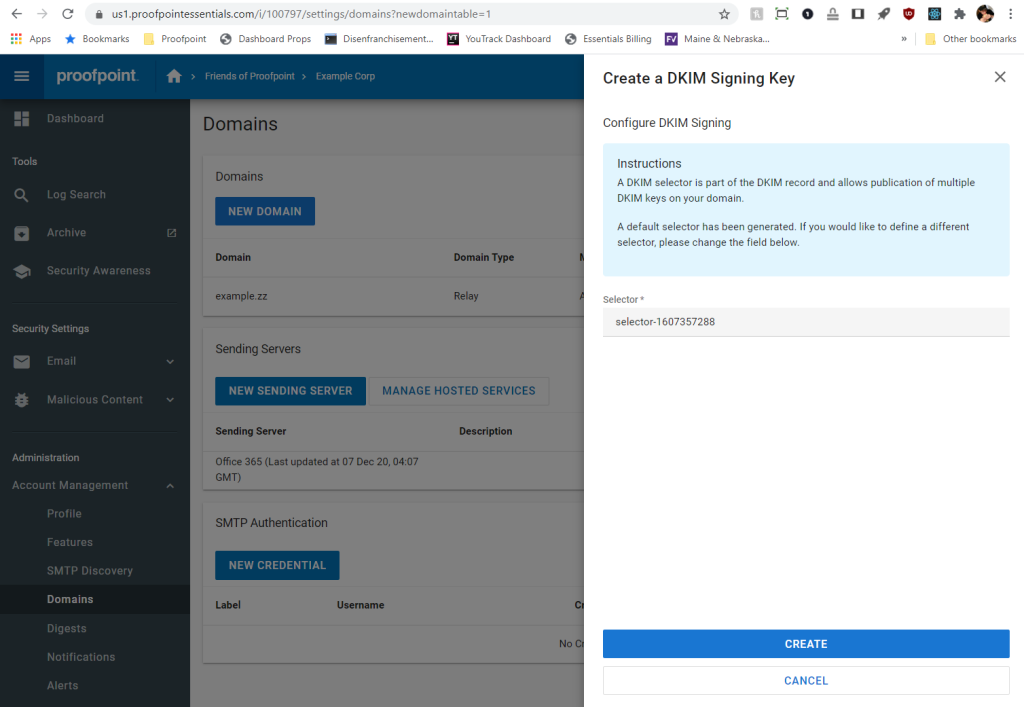
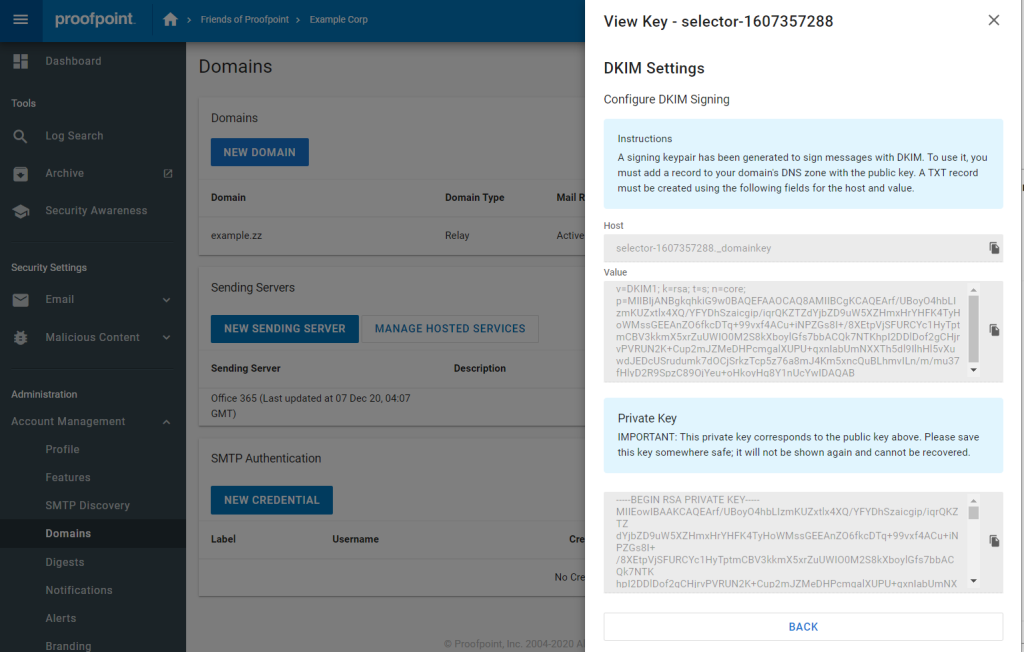
6. The resulting screen will give you the hostname and value into your DNS zone. You typically do this on your domain registrar’s website (GoDaddy, Dotster, Namecheap, etc.)
You are also given an opportunity to save the private key to a secure location, in case you need it in the future. This is the only time this value will be displayed.
7. Once you’ve made the addition to your DNS zone, Proofpoint Essentials will need to validate that the record was added correctly. To do so, click the Verify Key button in the key’s context menu.
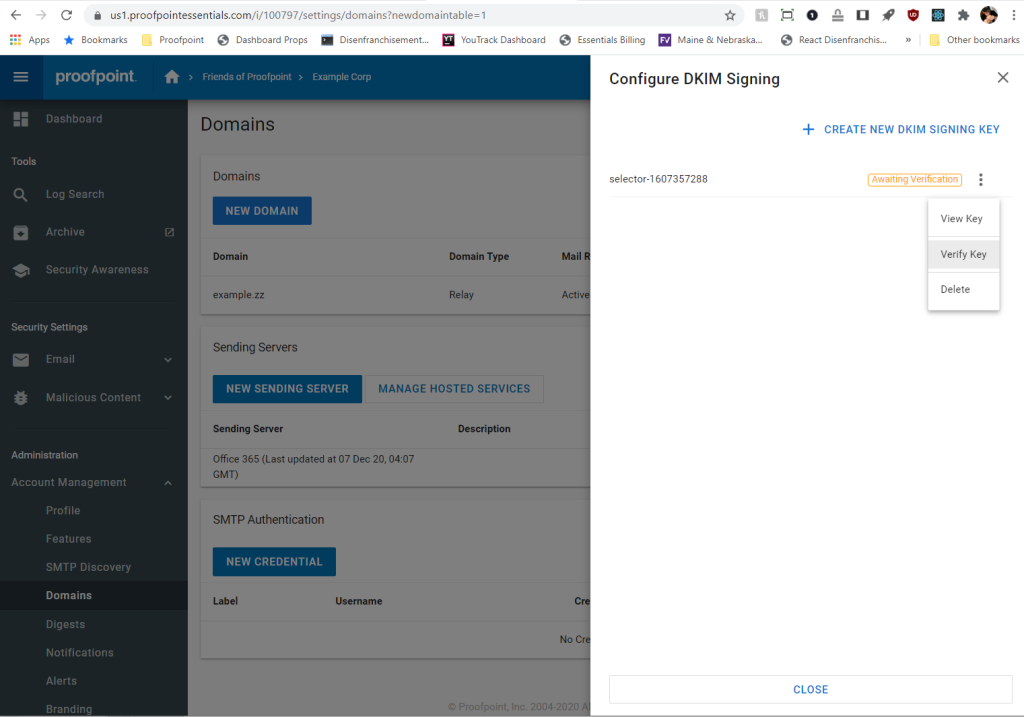
8. Once the key is successfully verified, outbound DKIM signing is automatically enabled for this domain. You can disable signing at any time by using the vertical ellipsis on the right-hand side of the Domains table. Click the option labelled Disable DKIM.
Use our free DKIM record lookup tool to validate the published DKIM record.
You can use Skysnag’s free DKIM Checker to check the health of your DKIM record here
Enable DMARC for your domains to protect against spoofing. Sign up for a free trial today!





